Set up corporate login (Single Sign-On)
This topic describes how to configure a corporate login using Single Sign-On (SSO) for the users in your TrueContext team.
Available on the Enterprise tier only:
Contents
About
TrueContext provides Security Assertion Markup Language (SAML) based Corporate Login/Single Sign-On (SSO). This allows users to log in to TrueContext using their corporate credentials. TrueContext Corporate Login can be used with a number of identity providers, including Okta, OneLogin, Microsoft Entra ID, and Active Directory Federation Services (ADFS).
Beyond ease of login, enabling Single Sign-On on a team provides extra security features. Organizations can easily manage all user credentials through a single identity provider. It is also possible to set a maximum session length for TrueContext, so users are required to re-authenticate after a set period of inactivity.
Note:With your security in mind, TrueContext only supports an SP-initiated SSO flow. This means that the user must initiate the login process by accessing the TrueContext portal. TrueContext does not support an IdP-initiated SSO flow.
What is Corporate Login/Single Sign-On?
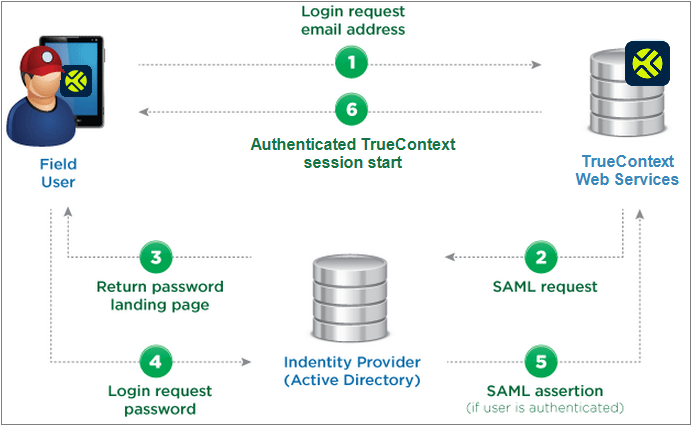
Security Assertion Markup Language (SAML) is an XML standard that enables single sign-on (SSO). SAML performs authorization (what parts of the service is a user allowed to access?) and authentication (is a user allowed access to a service?) between an identity provider (IdP) and a service provider (SP).
For example:
-
TrueContext is a service provider.
-
Active Directory, Okta, OneLogin, and similar services are identity providers.
With SSO, users that are authenticated on a commonly used IdP can log into sites like TrueContext using their corporate credentials. With centralized identity providers, SSO can be used to manage user IDs, passwords and associated authentications.
Note:TrueContext supports SAML 2.0.
How does enabling Corporate Login/SSO affect how users log in?
When enabled on a TrueContext team, SSO can be used to sign in to the TrueContext Web Portal![]() The TrueContext Web Portal is a web application used to manage security settings, forms, FormSpaces, other users, Data Sources, and Data Destinations., the iOS Mobile App, the Windows Mobile App, and the Android Mobile App.
The TrueContext Web Portal is a web application used to manage security settings, forms, FormSpaces, other users, Data Sources, and Data Destinations., the iOS Mobile App, the Windows Mobile App, and the Android Mobile App.
When users try to sign into TrueContext:
-
They will be prompted to enter their TrueContext username, email address, or team domain.
-
They will be redirected to their IdP.
-
Users log in to their IdP.
-
Users will be automatically logged in to TrueContext.
Users already authenticated on the IdP side are logged into TrueContext without entering any credentials.
See what it looks like to log in to TrueContext using single sign-on.
SSO and Multi-Factor Authentication
The
Tip:Your organization can use both MFA and SSO within your TrueContext implementation. For example, you can set up employee users for SSO and third-party contractor users for MFA native login.
Info:The topic Set Up Multi-Factor Authentication describes the available authentication methods in more detail.
User Management when using Corporate Login/SSO
Refer to this article to learn how to correctly set up your users.
Enable Corporate Login/Single Sign-On for a TrueContext Team
Note:With your security in mind, TrueContext only supports an SP-initiated SSO flow. This means that the user must initiate the login process by accessing the TrueContext portal. TrueContext does not support an IdP-initiated SSO flow.
In the web portal:
-
As a team admin, select your name on the top right of the screen, and then select Team Settings.
-
Select Security.
-
Select Single Sign-On > Update.
-
Set up the team Single Sign-On settings as detailed below.
Single Sign-On Configuration
Team Domain
This is the team domain that users can enter on the TrueContext login page when using single sign-on. For example, <companyname>.
Username Suffix (optional)
Usernames of TrueContext users on an SSO-enabled team must match the usernames on the team's IdP.
The "username suffix" can be entered if the TrueContext usernames have additional characters (so they are unique in the TrueContext system).
For example, if the TrueContext username is "johndoe@yourcompany.com", but the username when logging into the IdP provider is "johndoe", enter "@yourcompany.com" as the username suffix.
Problem Contact Email
Enter the email address of the person who can help users log in if their corporate credentials are not working.
Note:Remember that our technical support team can’t help users who “Must use Corporate Single Sign-On” with logging in, as their login credentials are not actually in the TrueContext system.
If our system detects that a user is having trouble logging in (trying to reset their password, multiple failed login attempts) we will send the user an email reminding them to use their corporate credentials and directing them to contact the Problem Contact person if they need assistance with those credentials.
When your users who use Corporate Login contact TrueContext Support for help with their credentials, our Support team will redirect users to the Problem Contact email address.
Launching Corporate Login directly from an Identity Provider
Although TrueContext doesn’t support an IdP-initiated flow for SSO, you can configure your IdP to launch the TrueContext portal from the main IdP dashboard. When the TrueContext portal opens, it prompts users to sign in with their corporate login credentials.
Use the following URL when you configure the IdP:
https://live.prontoforms.com/security/login/saml?domain=<SSO team domain>
To support existing integrations, some items will continue to use “prontoforms” or “pf” in the domain or code.
For more detailed information about what’s changing, visit https://support.truecontext.com/hc/en-us/articles/19516168513556
Identity Provider Metadata
Note:Remember that you must configure SSO in both TrueContext and in your identity provider.
Identity provider metadata is how SAML authenticates usernames and logins.
Upload Metadata File
Upload the metadata file provided by your IdP.
Get Service Provider Metadata from TrueContext
In order to complete the SAML configuration on the IdP side, the IdP will require service provider metadata from TrueContext.
Note:If your IdP requires a unique entity ID for each of your TrueContext teams, contact support@truecontext.com. The Support team will start the process of setting you up with a unique entity ID per team.
-
Select the Security tab.
-
Select Single Sign-On > Download Service Provider Metadata.
-
Provide this file to the IdP where required.
Note:Remember that you must configure SSO in both TrueContext and in your identity provider.